Temporary Passcode Authentication
1682030036057
On March 31, 2023, the Email Gateway Defense (EGD) team published an update that disabled auto-authentication for end users from quarantine email digests. End users are now required to authenticate before they can view their account and make updates to their quarantined mail. With this update, many users of shared mailboxes and distribution lists were no longer able to manage the quarantine messages themselves and instead had to reach out to their administrators for assistance.
The Email Gateway Defense (EGD) team has implemented a temporary passcode authentication method to allow users to access their shared mailbox and distribution list accounts. On April 25, 2023, this solution will be released to customers. Please see below for a step-by-step guide on how to enable and sign into EGD using temporary passcodes.
Note: This sign-in method is optional. If you choose not to enable temporary passcode authentication for users, your sign-in flow will be unchanged.
HOW IT WORKS
Here’s a quick overview of how users can sign into EGD with temporary passcodes:
The administrator of an account will enable temporary passcode authentication on an account or domain level (or both). See Enabling Temporary Passcodes section below. This feature will create the below sign-in scenarios:
If both SSO and temporary passcodes are enabled, users can choose to continue with normal SSO login or request a temporary passcode.
If SSO is enabled but temporary passcodes are disabled, users will sign in through SSO as usual and will not be given the option to request a temporary passcode.
If SSO is disabled but temporary passcodes are enabled, users will have the option to log in with their EGD credentials or request a temporary passcode.
If both SSO and temporary passcodes are disabled, users will have to sign in with their EGD email and password credentials.
User clicks on a link in quarantine digest email and is prompted to log into EGD at https://ess.barracudanetworks.com/.
Instead of logging in with account password credentials, the user is given an option to request a temporary passcode. See Signing In with Temporary Passcodes section below for a step-by-step guide.
User requests the temporary passcode and an email containing the passcode is sent to the shared inbox. The passcode is valid for 15 minutes. The user copies and pastes the passcode into the sign-in field on their open browser window.
The user is then authenticated into EGD and can manage their quarantined mail, view their message log, and utilize the actions (Deliver, Allow List, Block List) from the digest email as expected. User is also authenticated for their entire 24-hour browser session.
Here’s a demo video describing the process: https://share.vidyard.com/watch/G1GvuwKtM6nE6iG3kt5zMf
ENABLING TEMPORARY PASSCODES (ADMIN SETTING)
Upon release, the temporary passcode authentication process will be set to disabled by default. To enable temporary passcode authentication for your users, the administrator of the account must follow the below steps:
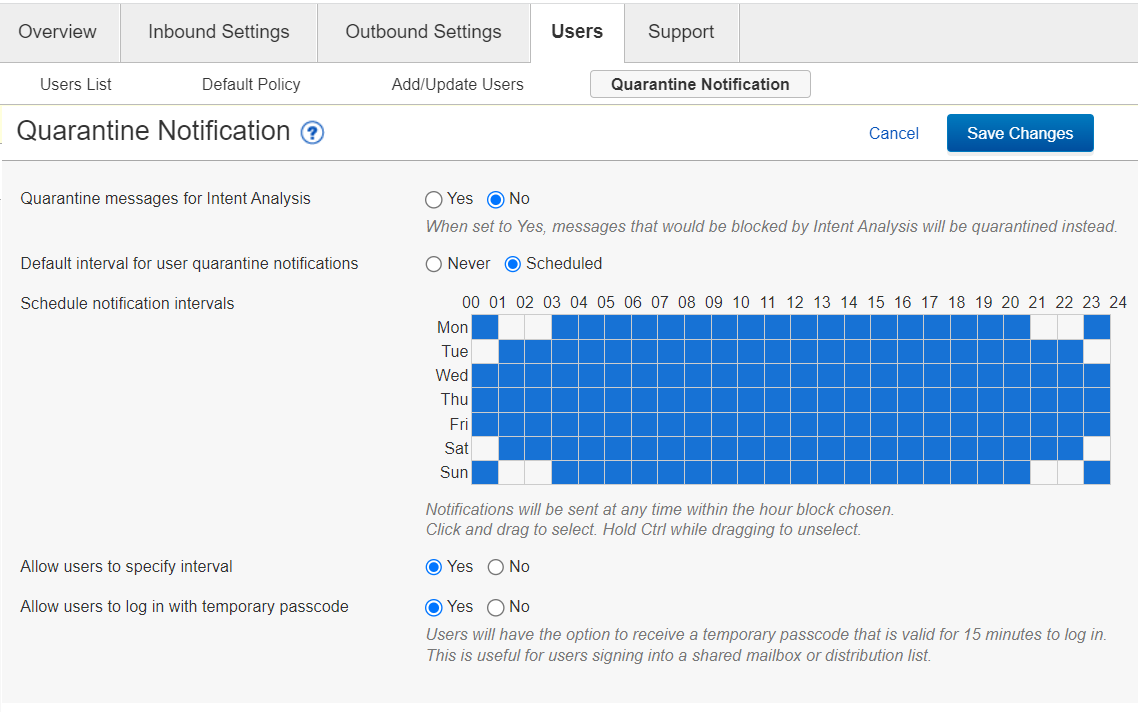
Account administrator signs into EGD
Click on Users tab
Click on Quarantine Notification tab
See new feature Allow users to sign in with temporary passcode (set to No by default)
To enable, select Yes for this feature
Click the Save Changes button on top right-hand side of the page
Temporary passcodes authentication is now an option for all users in this account
Note: If you’d like to enable for only a specific domain, sign in as domain administrator and follow the same steps above
SIGNING IN WITH TEMPORARY PASSCODES
Once the admin setting is enabled, the users of a shared mailbox or distribution list will see a new option when they attempt to sign into the shared email address. See below for a step-by-step guide to authenticating with a temporary passcode:
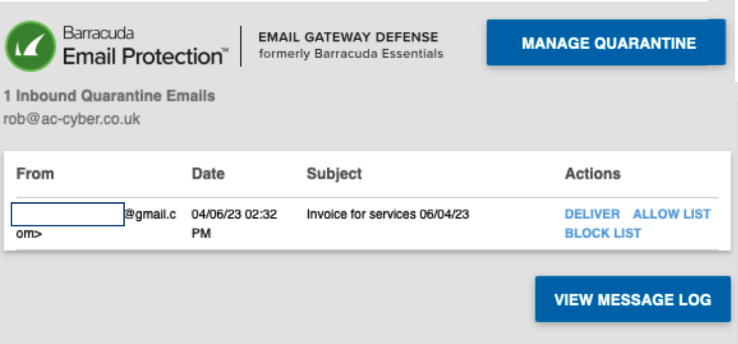
User clicks on a link or button in their quarantine digest email (Manage Quarantine, View Message Log, Deliver, Allow List, Block List) or goes to directly to EGD site: https://ess.barracudanetworks.com/
User is prompted to sign into EGD
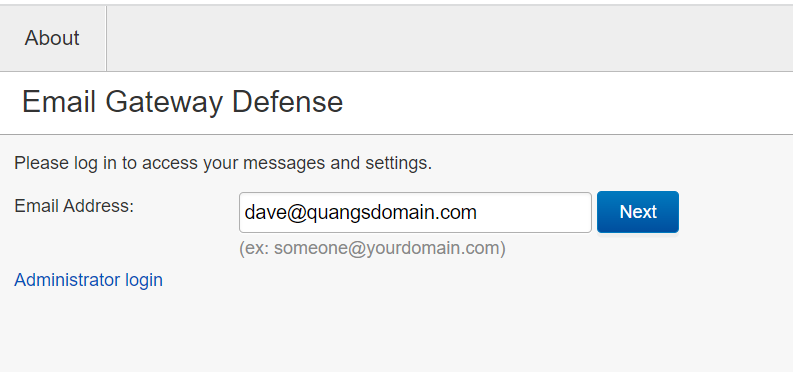
User enters shared inbox or distribution list email address in Email Address field and clicks the Next button
If account is SSO enabled, user will see an intermediary page to allow them to choose between continuing with SSO login (not for shared email addresses) or shown the option to request a temporary passcode
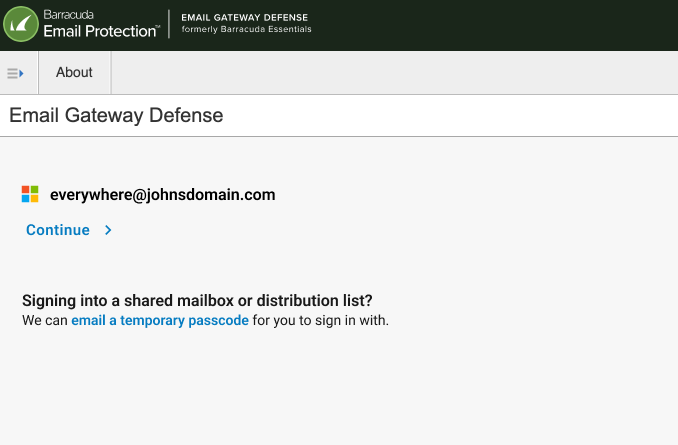
If account does not have SSO enabled, user will be prompted to enter their password or shown the option to request a temporary passcode
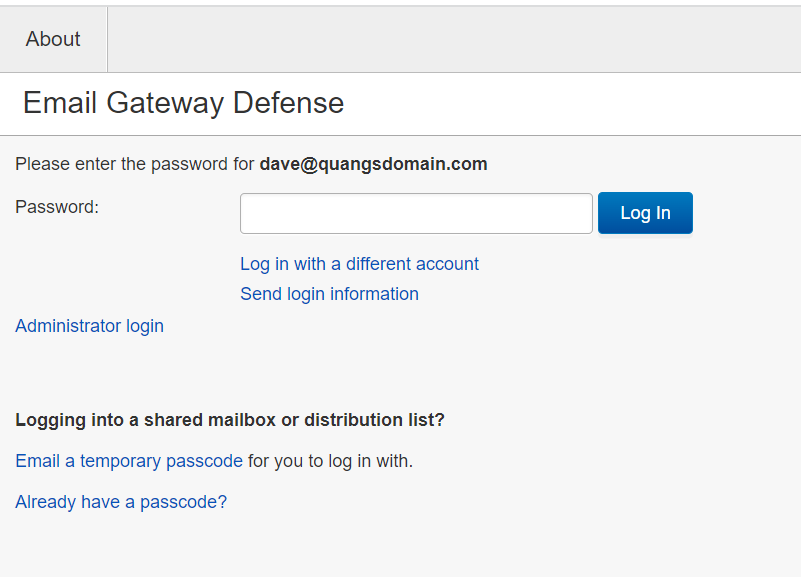
User clicks on email a temporary passcode to send the passcode to the shared mailbox (Note: Passcode is valid for 15 minutes)
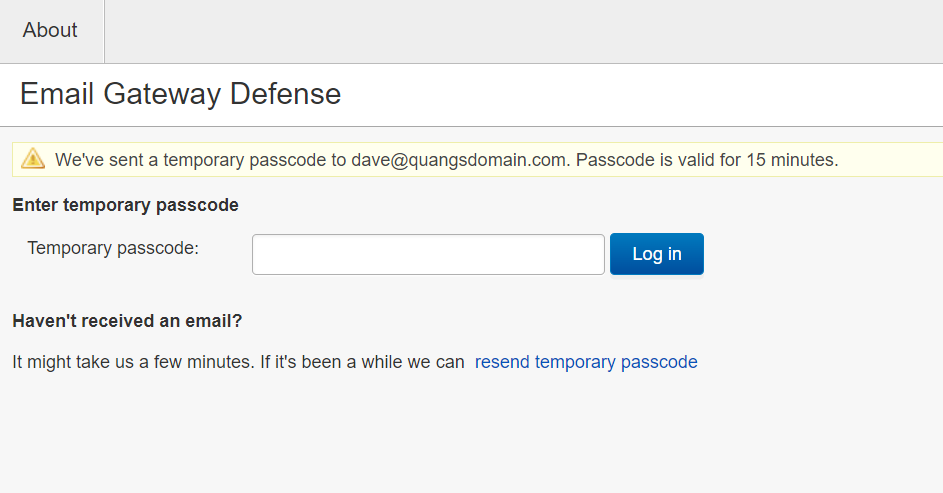
User receives an email to the shared inbox where they can copy the passcode and paste into Temporary passcode field (Note: Passcodes are case sensitive) and clicks Log in
Note: Users can also request a new passcode by clicking resend temporary passcode
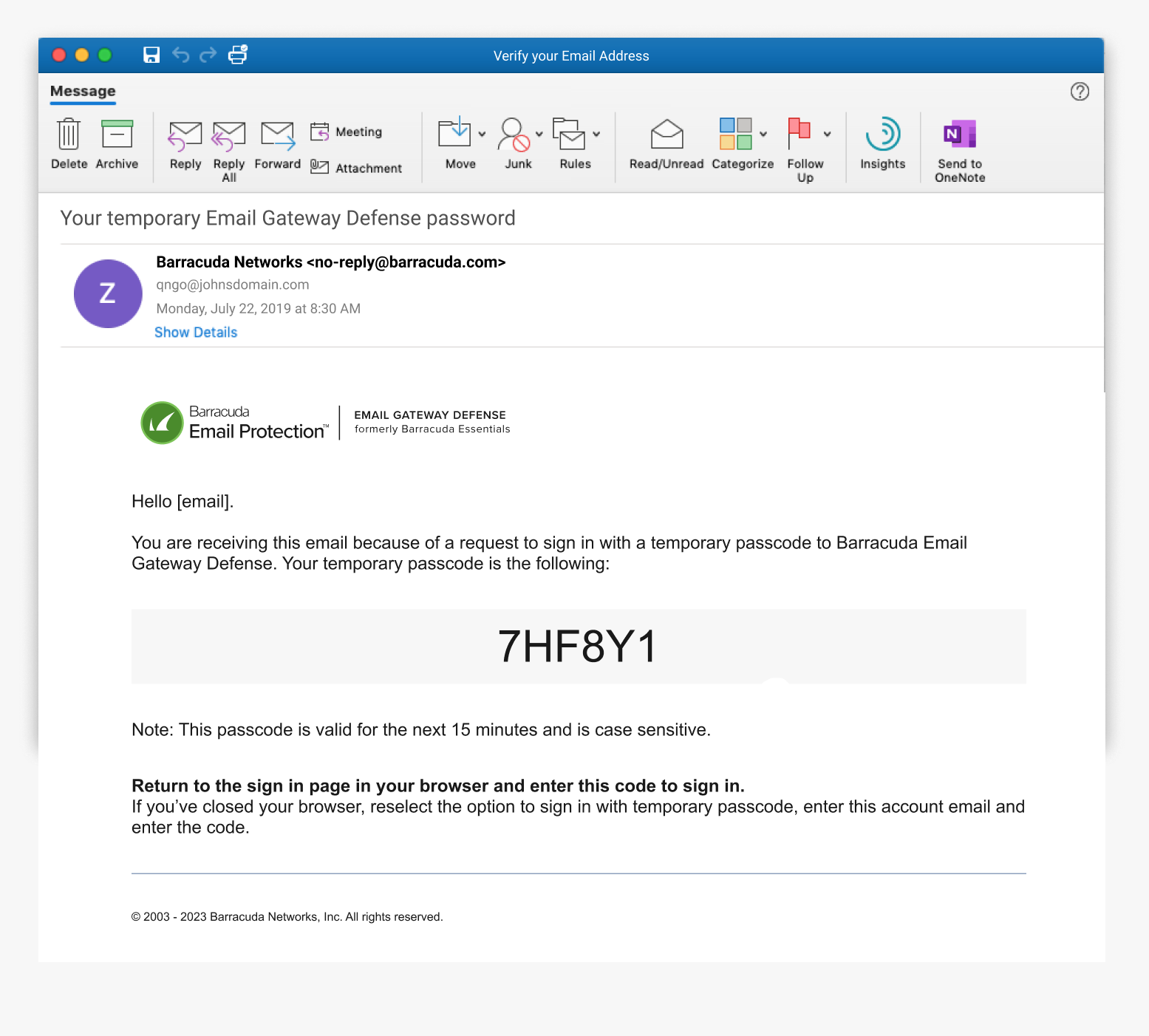
The user will then be signed into their Message Log and can manage their quarantine email
Now that the user has signed in with a temporary passcode, they are authenticated for the entire length of their browser session (24 hours)
The user can now use the Deliver, Allow List, Block List buttons on the quarantine digest email as expected
If you have any questions on the above process, please contact Barracuda Networks Technical Support https://www.barracuda.com/support.
Frequently Asked Questions (FAQs):
What if someone else in the shared mailbox also requests a temporary passcode?
If 2 users request a temporary passcode around the same time, 2 separate emails with different passcodes will be sent to the shared inbox. Both passcodes will be active for 15 minutes after they are requested, and either user can use either passcode within these 15 minutes. One passcode does not invalidate another. A passcode only becomes invalid after its 15-minute lifespan runs out.
Only 5 passcodes are active at one time for each account. If users have requested 5 passcodes within the same 15 minutes, no more passcodes can be requested. Any of the 5 active passcodes can be used to authenticate. Once 1 of the 5 passcodes expires, another temporary passcode can be requested.
How frequently do I need to sign in with a temporary passcode?
Once you have signed in with a temporary passcode, you are authenticated into the account for the length of your browser session which is 24 hours. After your browser session has ended, you will need to request another temporary passcode to start another 24-hour session.
What if my account uses SSO (Azure AD or LDAP) to log-in?
If your Admin has set up your account to use Azure AD or LDAP authentication with Single Sign-On, they will need to enable the temporary passcodes feature in the Enabling Temporary Passcode section above. This will allow the users to sign in with a temporary passcode for a shared mailbox. For non-shared email addresses, users will still be able to sign in with their AD or LDAP credentials.
How do I request a new temporary passcode?
Press the resend temporary passcode link on the Enter temporary passcode page. If requested for a shared mailbox or distribution group, please wait a couple of minutes before requesting a new passcode as multiple emails may be sent to everyone in your shared mailbox or distribution list.
What if I am still having trouble signing in?
Please contact Barracuda Networks Technical Support at https://www.barracuda.com/support to help you log in or escalate your issue to the correct team.
Related Campus Articles:
Did you like this update?
![]()
![]()
![]()
Leave your name and email so that we can reply to you (both fields are optional):