There are two enhancements that are being rolled out together:
Auth0 authentication for Azure users: https://campus.barracuda.com/doc/100368461/
New User Interface for end users: https://campus.barracuda.com/doc/96023030/
]]>
There are two enhancements that are being rolled out together:
Auth0 authentication for Azure users: https://campus.barracuda.com/doc/100368461/
New User Interface for end users: https://campus.barracuda.com/doc/96023030/
]]>
At approximately 3:09pm on May 22, 2023, a routine update to Email Gateway Defense's (EGD) spam scoring logic inadvertently caused customers' email scores to be increased by 2.9 pts. This unfortunately led to a significant amount of email messages to be blocked as false positives. The spam rule update was reverted, however a large number of users needed to sign onto EGD redeliver their incorrectly blocked messages.
At 4:30pm, the EGD team started to receive reports that the UI was experiencing an outage and customers were seeing a 504 timeout error when attempting to sign in and release their blocked mail. While we investigated the incident, the CAPTCHA login step was turned on for administrators in an abundance of caution. After investigation, it was determined that this UI outage in service was due to the web servers being overloaded by the large number of users trying to sign in and resend their mail at one time.
The EGD team tried to remediate this issue by refreshing and creating new web server instances to accommodate the much larger flow of traffic. While EGD has autoscaling settings in place to automatically fluctuate to changes in traffic patterns, these instances were incorrectly displaying as healthy and were not refreshing as needed. By 6:17pm, the fix to increase instance capacity for the web servers successfully accommodated the higher traffic and the UI returned to normal.
The following day, May 23, 2023, at approximately 2:38pm, the EGD team began hearing additional reports that the UI for the new React platform was displaying timeout errors ("link to login is invalid") for certain end users. The EGD team investigated and implemented a fix at 6:10pm for a log-in call to the database that was causing abnormally long load times. While this additional incident was not directly related to the spam scoring update, this problem was exacerbated by the higher than usual traffic attempting to log into the new UI to remediate their email.
The EGD team is currently investigating ways to prevent any future changes to spam scoring from leading to such a high number of emails being blocked as false positives. The team is also investigating ways to adjust autoscaling logic to prevent any loss in service in the future. We apologize for the inconvenience that this has caused to our customers.
Impact Timeline (All times in UTC)
2023-05-22:
03:09pm: Update to spam scoring logic was implemented inadvertently causing customer's email scores to be increased (leading to a large amount of false positives).
03:09pm-04:29pm: Users begin to log into EGD at a high rate to redeliver their incorrectly blocked email messages causing the web servers to be overloaded. CAPTCHA login step was implemented for administrators.
04:30pm: EGD team creates incident and begins investigation of UI outage.
05:02pm-05:56pm: Multiple attempts were made to refresh and replace unhealthy web server instances with healthy ones to accommodate for larger traffic patterns.
06:17pm: Traffic flow is back to being accommodated by the new healthy instances and the UI loads correctly for users.
2023-05-23:
02:38pm - The EGD team began receiving reports that the UI for the new React platform was displaying timeout errors ("link to login is invalid").
02:40pm - The team begins investigation team identifies problem with autoscaling capacity and implements fix.
06:10pm - A fix is implemented to a call in the log-in process that was causing abnormally long load times and the UI begins to load as expected.
Impact Duration
Initial Issue Start: May 22, 2023 @ 3:09pm UTC
Initial Issue End: May 22, 2023 @ 6:17pm UTC
Secondary Issue Start: May 23, 2023 @ 2:38pm UTC
Secondary Issue End: May 23, 2023 @ 6:10pm UTC
Incident Analysis
EGD's Web interface interruption for customers in the US region on May 22, 2023 was due to an autoscaling failure during increased traffic load. This higher traffic load was due to an update to spam scoring logic that caused a large amount of customer mail to be incorrectly blocked. As users logged in to manage their blocked mail, the web servers became overloaded and the UI failed to load. Once instances were refreshed successfully, the UI worked as expected. However, the following day, the new React platform web servers were also overloaded due to a call in the log-in process that was creating abnormally long load times. This call combined with the increased traffic caused the new UI login flow to be interrupted with timeout errors for customers. This problem was also remediated.
Corrective Actions
These are the areas being addressed as a result of this incident:
The EGD team is investigating the problem caused by the update to the spam scoring logic that caused many false positives.
The EGD team is investigating improvements in the incident resolution process for quicker identification of the problem and remediation planning.
The EGD team is investigating updates to the autoscaling logic for web servers to automatically accommodate higher traffic changes.
The EGD team is also investigating ways to allow users to more quickly and efficiently rescan and redeliver mail that may be blocked incorrectly due to an incident or setting update.
Next Steps for Customers
Unfortunately, as there was an extremely high number of affected customers and email, we are unable to manually rescan and redeliver mail that was incorrectly blocked due to this incident. We apologize for the inconvenience this has caused to our customers.
Please see below for the steps to allow end users to redeliver their mail. This will lessen the burden on administrators with a high number of emails to remediate.
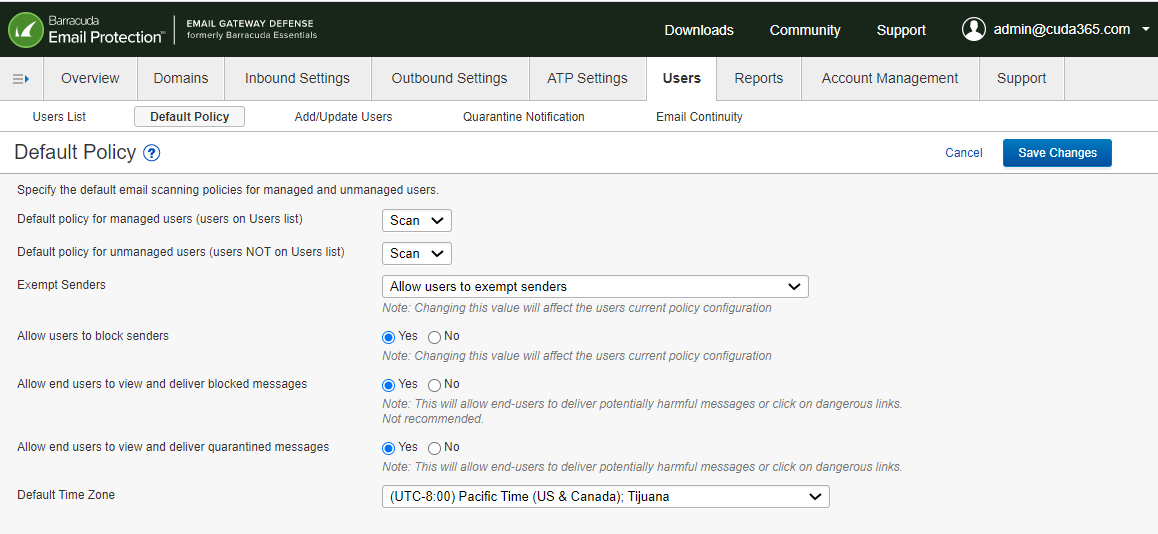
Admin signs into EGD under the Users tab, select Default Policy
Set the setting labelled Allow end users to view and deliver blocked messages to Yes (if this is set to off) and click Save Changes
Now users will be able to login and deliver their incorrectly blocked mail. Note: this will potentially allow the users to send mail that should not be delivered, so please advise users to proceed with caution. If admins are concerned about future user behavior, they can reset this setting to No after mail has been delivered from this May 22, 2023 incident.
At approximately 3:09pm on May 22, 2023, a routine update to Email Gateway Defense's (EGD) spam scoring logic inadvertently caused customers' email scores to be increased by 2.9 pts. This unfortunately led to a significant amount of email messages to be blocked as false positives. The spam rule update was reverted, however a large number of users needed to sign onto EGD redeliver their incorrectly blocked messages.
At 4:30pm, the EGD team started to receive reports that the UI was experiencing an outage and customers were seeing a 504 timeout error when attempting to sign in and release their blocked mail. While we investigated the incident, the CAPTCHA login step was turned on for administrators in an abundance of caution. After investigation, it was determined that this UI outage in service was due to the web servers being overloaded by the large number of users trying to sign in and resend their mail at one time.
The EGD team tried to remediate this issue by refreshing and creating new web server instances to accommodate the much larger flow of traffic. While EGD has autoscaling settings in place to automatically fluctuate to changes in traffic patterns, these instances were incorrectly displaying as healthy and were not refreshing as needed. By 6:17pm, the fix to increase instance capacity for the web servers successfully accommodated the higher traffic and the UI returned to normal.
The following day, May 23, 2023, at approximately 2:38pm, the EGD team began hearing additional reports that the UI for the new React platform was displaying timeout errors ("link to login is invalid") for certain end users. The EGD team investigated and implemented a fix at 6:10pm for a log-in call to the database that was causing abnormally long load times. While this additional incident was not directly related to the spam scoring update, this problem was exacerbated by the higher than usual traffic attempting to log into the new UI to remediate their email.
The EGD team is currently investigating ways to prevent any future changes to spam scoring from leading to such a high number of emails being blocked as false positives. The team is also investigating ways to adjust autoscaling logic to prevent any loss in service in the future. We apologize for the inconvenience that this has caused to our customers.
Impact Timeline (All times in UTC)
2023-05-22:
03:09pm: Update to spam scoring logic was implemented inadvertently causing customer's email scores to be increased (leading to a large amount of false positives).
03:09pm-04:29pm: Users begin to log into EGD at a high rate to redeliver their incorrectly blocked email messages causing the web servers to be overloaded. CAPTCHA login step was implemented for administrators.
04:30pm: EGD team creates incident and begins investigation of UI outage.
05:02pm-05:56pm: Multiple attempts were made to refresh and replace unhealthy web server instances with healthy ones to accommodate for larger traffic patterns.
06:17pm: Traffic flow is back to being accommodated by the new healthy instances and the UI loads correctly for users.
2023-05-23:
02:38pm - The EGD team began receiving reports that the UI for the new React platform was displaying timeout errors ("link to login is invalid").
02:40pm - The team begins investigation team identifies problem with autoscaling capacity and implements fix.
06:10pm - A fix is implemented to a call in the log-in process that was causing abnormally long load times and the UI begins to load as expected.
Impact Duration
Initial Issue Start: May 22, 2023 @ 3:09pm UTC
Initial Issue End: May 22, 2023 @ 6:17pm UTC
Secondary Issue Start: May 23, 2023 @ 2:38pm UTC
Secondary Issue End: May 23, 2023 @ 6:10pm UTC
Incident Analysis
EGD's Web interface interruption for customers in the US region on May 22, 2023 was due to an autoscaling failure during increased traffic load. This higher traffic load was due to an update to spam scoring logic that caused a large amount of customer mail to be incorrectly blocked. As users logged in to manage their blocked mail, the web servers became overloaded and the UI failed to load. Once instances were refreshed successfully, the UI worked as expected. However, the following day, the new React platform web servers were also overloaded due to a call in the log-in process that was creating abnormally long load times. This call combined with the increased traffic caused the new UI login flow to be interrupted with timeout errors for customers. This problem was also remediated.
Corrective Actions
These are the areas being addressed as a result of this incident:
The EGD team is investigating the problem caused by the update to the spam scoring logic that caused many false positives.
The EGD team is investigating improvements in the incident resolution process for quicker identification of the problem and remediation planning.
The EGD team is investigating updates to the autoscaling logic for web servers to automatically accommodate higher traffic changes.
The EGD team is also investigating ways to allow users to more quickly and efficiently rescan and redeliver mail that may be blocked incorrectly due to an incident or setting update.
Next Steps for Customers
Unfortunately, as there was an extremely high number of affected customers and email, we are unable to manually rescan and redeliver mail that was incorrectly blocked due to this incident. We apologize for the inconvenience this has caused to our customers.
Please see below for the steps to allow end users to redeliver their mail. This will lessen the burden on administrators with a high number of emails to remediate.
Admin signs into EGD under the Users tab, select Default Policy
Set the setting labelled Allow end users to view and deliver blocked messages to Yes (if this is set to off) and click Save Changes
Now users will be able to login and deliver their incorrectly blocked mail. Note: this will potentially allow the users to send mail that should not be delivered, so please advise users to proceed with caution. If admins are concerned about future user behavior, they can reset this setting to No after mail has been delivered from this May 22, 2023 incident.

The Email Gateway Defense (EGD) team has implemented a temporary passcode authentication method to allow users to access their shared mailbox and distribution list accounts. On April 25, 2023, this solution will be released to customers. Please see below for a step-by-step guide on how to enable and sign into EGD using temporary passcodes.
Note: This sign-in method is optional. If you choose not to enable temporary passcode authentication for users, your sign-in flow will be unchanged.
HOW IT WORKS
Here’s a quick overview of how users can sign into EGD with temporary passcodes:
The administrator of an account will enable temporary passcode authentication on an account or domain level (or both). See Enabling Temporary Passcodes section below. This feature will create the below sign-in scenarios:
If both SSO and temporary passcodes are enabled, users can choose to continue with normal SSO login or request a temporary passcode.
If SSO is enabled but temporary passcodes are disabled, users will sign in through SSO as usual and will not be given the option to request a temporary passcode.
If SSO is disabled but temporary passcodes are enabled, users will have the option to log in with their EGD credentials or request a temporary passcode.
If both SSO and temporary passcodes are disabled, users will have to sign in with their EGD email and password credentials.
User clicks on a link in quarantine digest email and is prompted to log into EGD at https://ess.barracudanetworks.com/.
Instead of logging in with account password credentials, the user is given an option to request a temporary passcode. See Signing In with Temporary Passcodes section below for a step-by-step guide.
User requests the temporary passcode and an email containing the passcode is sent to the shared inbox. The passcode is valid for 15 minutes. The user copies and pastes the passcode into the sign-in field on their open browser window.
The user is then authenticated into EGD and can manage their quarantined mail, view their message log, and utilize the actions (Deliver, Allow List, Block List) from the digest email as expected. User is also authenticated for their entire 24-hour browser session.
Here’s a demo video describing the process: https://share.vidyard.com/watch/G1GvuwKtM6nE6iG3kt5zMf
ENABLING TEMPORARY PASSCODES (ADMIN SETTING)
Upon release, the temporary passcode authentication process will be set to disabled by default. To enable temporary passcode authentication for your users, the administrator of the account must follow the below steps:
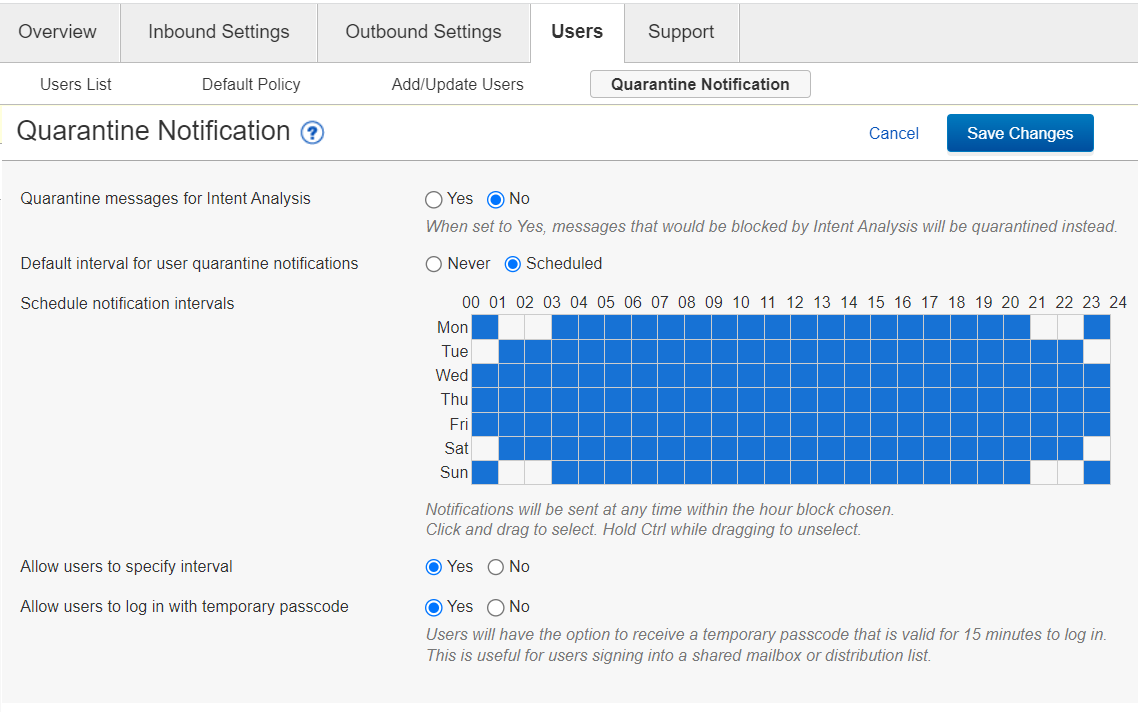
Account administrator signs into EGD
Click on Users tab
Click on Quarantine Notification tab
See new feature Allow users to sign in with temporary passcode (set to No by default)
To enable, select Yes for this feature
Click the Save Changes button on top right-hand side of the page
Temporary passcodes authentication is now an option for all users in this account
Note: If you’d like to enable for only a specific domain, sign in as domain administrator and follow the same steps above
SIGNING IN WITH TEMPORARY PASSCODES
Once the admin setting is enabled, the users of a shared mailbox or distribution list will see a new option when they attempt to sign into the shared email address. See below for a step-by-step guide to authenticating with a temporary passcode:
User clicks on a link or button in their quarantine digest email (Manage Quarantine, View Message Log, Deliver, Allow List, Block List) or goes to directly to EGD site: https://ess.barracudanetworks.com/
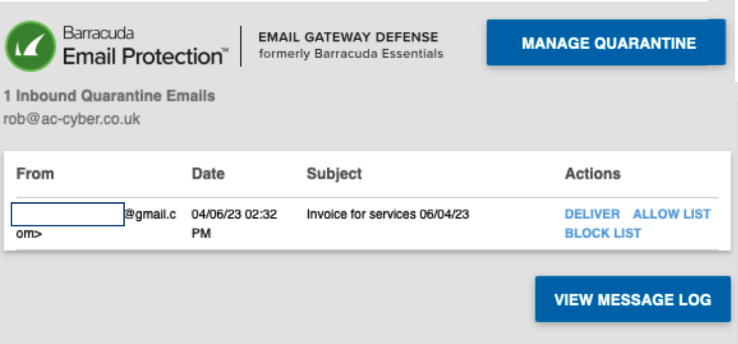
User is prompted to sign into EGD
User enters shared inbox or distribution list email address in Email Address field and clicks the Next button
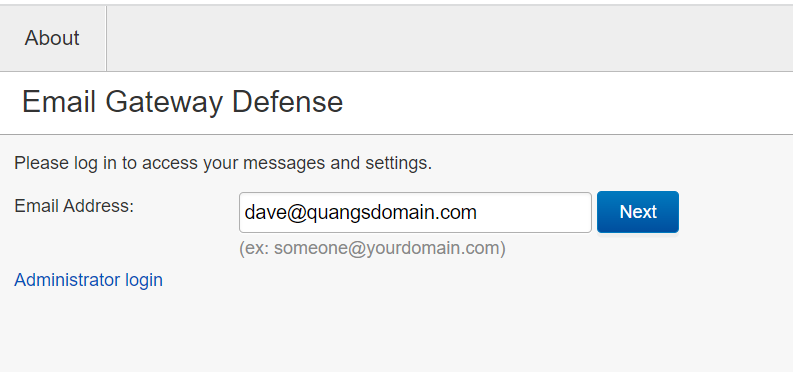
If account is SSO enabled, user will see an intermediary page to allow them to choose between continuing with SSO login (not for shared email addresses) or shown the option to request a temporary passcode
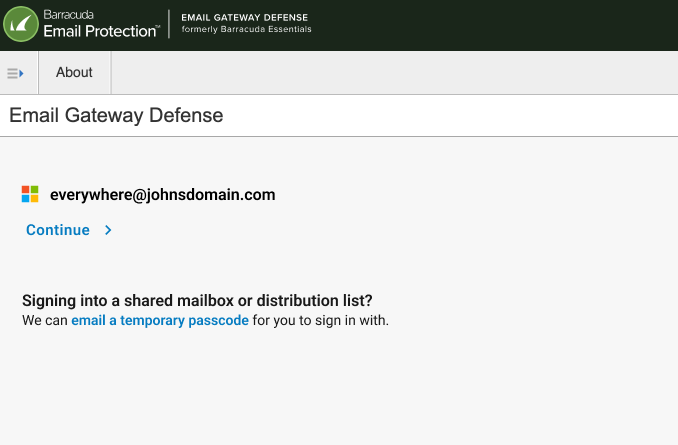
If account does not have SSO enabled, user will be prompted to enter their password or shown the option to request a temporary passcode
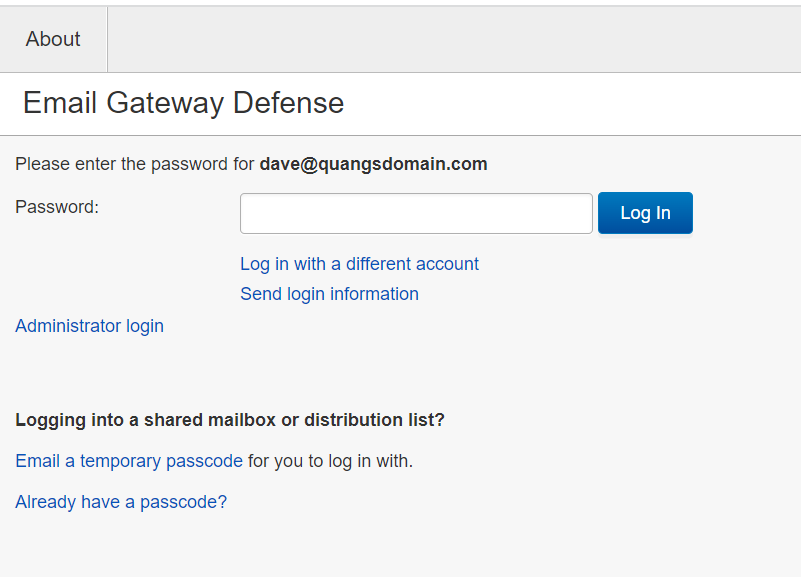
User clicks on email a temporary passcode to send the passcode to the shared mailbox (Note: Passcode is valid for 15 minutes)
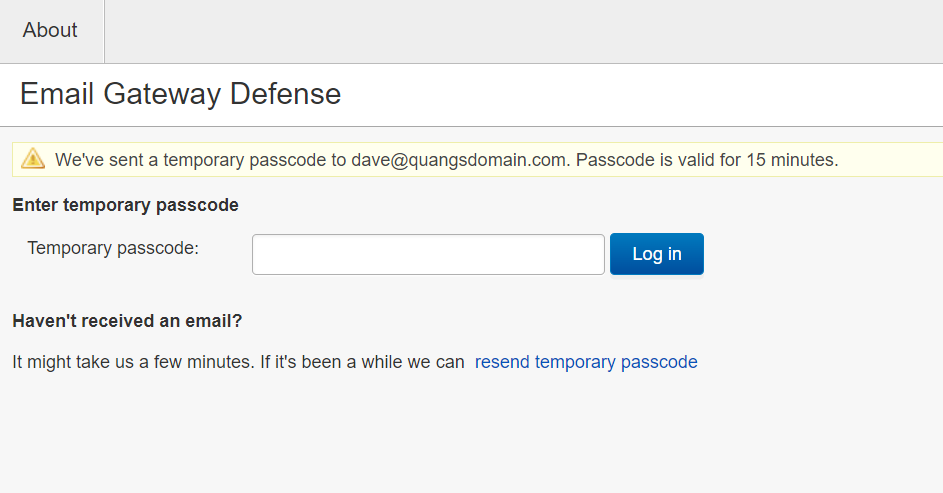
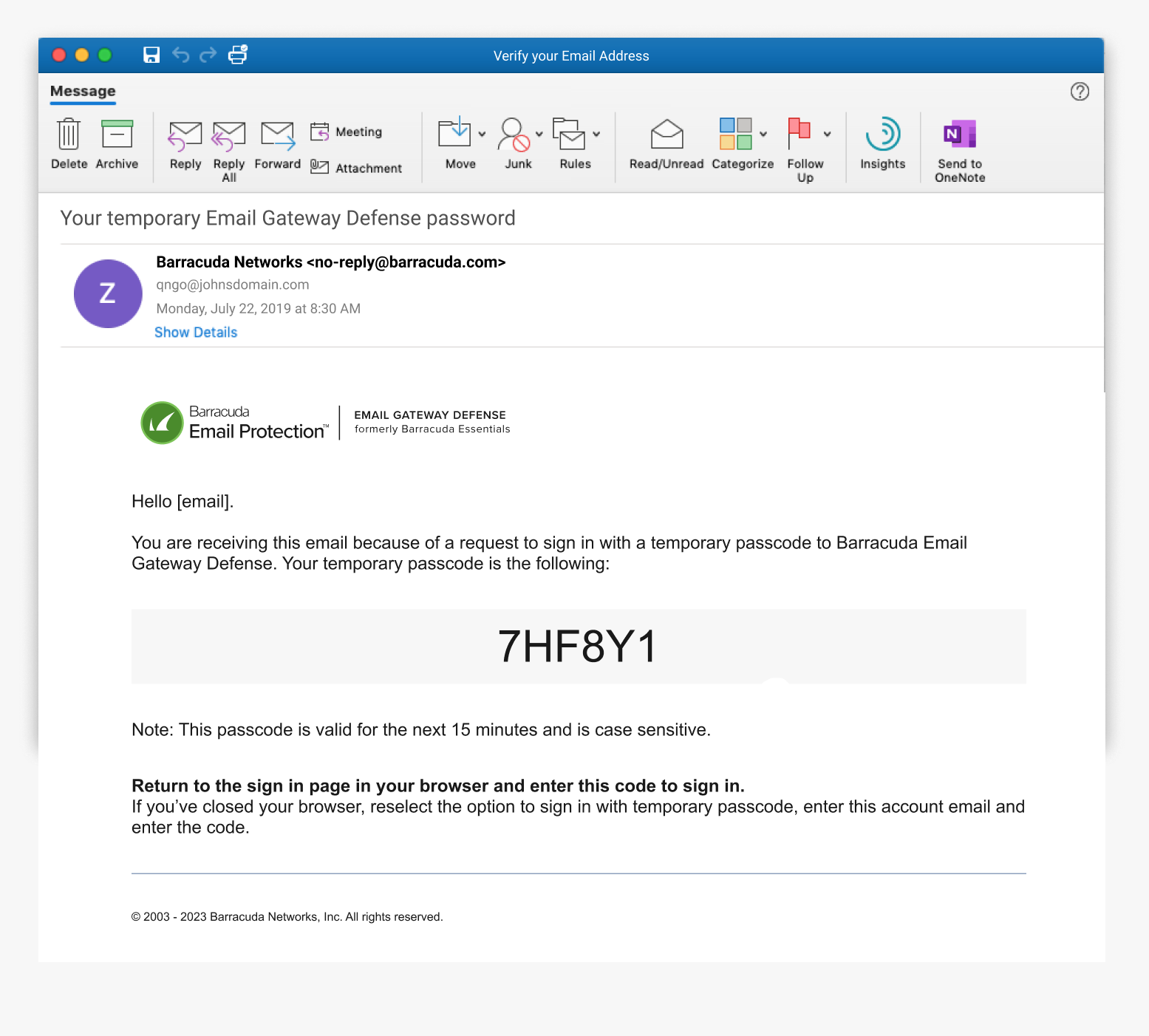
User receives an email to the shared inbox where they can copy the passcode and paste into Temporary passcode field (Note: Passcodes are case sensitive) and clicks Log in
Note: Users can also request a new passcode by clicking resend temporary passcode
The user will then be signed into their Message Log and can manage their quarantine email
Now that the user has signed in with a temporary passcode, they are authenticated for the entire length of their browser session (24 hours)
The user can now use the Deliver, Allow List, Block List buttons on the quarantine digest email as expected
If you have any questions on the above process, please contact Barracuda Networks Technical Support https://www.barracuda.com/support.
Frequently Asked Questions (FAQs):
What if someone else in the shared mailbox also requests a temporary passcode?
If 2 users request a temporary passcode around the same time, 2 separate emails with different passcodes will be sent to the shared inbox. Both passcodes will be active for 15 minutes after they are requested, and either user can use either passcode within these 15 minutes. One passcode does not invalidate another. A passcode only becomes invalid after its 15-minute lifespan runs out.
Only 5 passcodes are active at one time for each account. If users have requested 5 passcodes within the same 15 minutes, no more passcodes can be requested. Any of the 5 active passcodes can be used to authenticate. Once 1 of the 5 passcodes expires, another temporary passcode can be requested.
How frequently do I need to sign in with a temporary passcode?
Once you have signed in with a temporary passcode, you are authenticated into the account for the length of your browser session which is 24 hours. After your browser session has ended, you will need to request another temporary passcode to start another 24-hour session.
What if my account uses SSO (Azure AD or LDAP) to log-in?
If your Admin has set up your account to use Azure AD or LDAP authentication with Single Sign-On, they will need to enable the temporary passcodes feature in the Enabling Temporary Passcode section above. This will allow the users to sign in with a temporary passcode for a shared mailbox. For non-shared email addresses, users will still be able to sign in with their AD or LDAP credentials.
How do I request a new temporary passcode?
Press the resend temporary passcode link on the Enter temporary passcode page. If requested for a shared mailbox or distribution group, please wait a couple of minutes before requesting a new passcode as multiple emails may be sent to everyone in your shared mailbox or distribution list.
What if I am still having trouble signing in?
Please contact Barracuda Networks Technical Support at https://www.barracuda.com/support to help you log in or escalate your issue to the correct team.
Related Campus Articles:
]]>The Email Gateway Defense (EGD) team has implemented a temporary passcode authentication method to allow users to access their shared mailbox and distribution list accounts. On April 25, 2023, this solution will be released to customers. Please see below for a step-by-step guide on how to enable and sign into EGD using temporary passcodes.
Note: This sign-in method is optional. If you choose not to enable temporary passcode authentication for users, your sign-in flow will be unchanged.
HOW IT WORKS
Here’s a quick overview of how users can sign into EGD with temporary passcodes:
The administrator of an account will enable temporary passcode authentication on an account or domain level (or both). See Enabling Temporary Passcodes section below. This feature will create the below sign-in scenarios:
If both SSO and temporary passcodes are enabled, users can choose to continue with normal SSO login or request a temporary passcode.
If SSO is enabled but temporary passcodes are disabled, users will sign in through SSO as usual and will not be given the option to request a temporary passcode.
If SSO is disabled but temporary passcodes are enabled, users will have the option to log in with their EGD credentials or request a temporary passcode.
If both SSO and temporary passcodes are disabled, users will have to sign in with their EGD email and password credentials.
User clicks on a link in quarantine digest email and is prompted to log into EGD at https://ess.barracudanetworks.com/.
Instead of logging in with account password credentials, the user is given an option to request a temporary passcode. See Signing In with Temporary Passcodes section below for a step-by-step guide.
User requests the temporary passcode and an email containing the passcode is sent to the shared inbox. The passcode is valid for 15 minutes. The user copies and pastes the passcode into the sign-in field on their open browser window.
The user is then authenticated into EGD and can manage their quarantined mail, view their message log, and utilize the actions (Deliver, Allow List, Block List) from the digest email as expected. User is also authenticated for their entire 24-hour browser session.
Here’s a demo video describing the process: https://share.vidyard.com/watch/G1GvuwKtM6nE6iG3kt5zMf
ENABLING TEMPORARY PASSCODES (ADMIN SETTING)
Upon release, the temporary passcode authentication process will be set to disabled by default. To enable temporary passcode authentication for your users, the administrator of the account must follow the below steps:
Account administrator signs into EGD
Click on Users tab
Click on Quarantine Notification tab
See new feature Allow users to sign in with temporary passcode (set to No by default)
To enable, select Yes for this feature
Click the Save Changes button on top right-hand side of the page
Temporary passcodes authentication is now an option for all users in this account
Note: If you’d like to enable for only a specific domain, sign in as domain administrator and follow the same steps above

SIGNING IN WITH TEMPORARY PASSCODES
Once the admin setting is enabled, the users of a shared mailbox or distribution list will see a new option when they attempt to sign into the shared email address. See below for a step-by-step guide to authenticating with a temporary passcode:
User clicks on a link or button in their quarantine digest email (Manage Quarantine, View Message Log, Deliver, Allow List, Block List) or goes to directly to EGD site: https://ess.barracudanetworks.com/

User is prompted to sign into EGD
User enters shared inbox or distribution list email address in Email Address field and clicks the Next button

If account is SSO enabled, user will see an intermediary page to allow them to choose between continuing with SSO login (not for shared email addresses) or shown the option to request a temporary passcode

If account does not have SSO enabled, user will be prompted to enter their password or shown the option to request a temporary passcode

User clicks on email a temporary passcode to send the passcode to the shared mailbox (Note: Passcode is valid for 15 minutes)

User receives an email to the shared inbox where they can copy the passcode and paste into Temporary passcode field (Note: Passcodes are case sensitive) and clicks Log in
Note: Users can also request a new passcode by clicking resend temporary passcode

The user will then be signed into their Message Log and can manage their quarantine email
Now that the user has signed in with a temporary passcode, they are authenticated for the entire length of their browser session (24 hours)
The user can now use the Deliver, Allow List, Block List buttons on the quarantine digest email as expected
If you have any questions on the above process, please contact Barracuda Networks Technical Support https://www.barracuda.com/support.
Frequently Asked Questions (FAQs):
What if someone else in the shared mailbox also requests a temporary passcode?
If 2 users request a temporary passcode around the same time, 2 separate emails with different passcodes will be sent to the shared inbox. Both passcodes will be active for 15 minutes after they are requested, and either user can use either passcode within these 15 minutes. One passcode does not invalidate another. A passcode only becomes invalid after its 15-minute lifespan runs out.
Only 5 passcodes are active at one time for each account. If users have requested 5 passcodes within the same 15 minutes, no more passcodes can be requested. Any of the 5 active passcodes can be used to authenticate. Once 1 of the 5 passcodes expires, another temporary passcode can be requested.
How frequently do I need to sign in with a temporary passcode?
Once you have signed in with a temporary passcode, you are authenticated into the account for the length of your browser session which is 24 hours. After your browser session has ended, you will need to request another temporary passcode to start another 24-hour session.
What if my account uses SSO (Azure AD or LDAP) to log-in?
If your Admin has set up your account to use Azure AD or LDAP authentication with Single Sign-On, they will need to enable the temporary passcodes feature in the Enabling Temporary Passcode section above. This will allow the users to sign in with a temporary passcode for a shared mailbox. For non-shared email addresses, users will still be able to sign in with their AD or LDAP credentials.
How do I request a new temporary passcode?
Press the resend temporary passcode link on the Enter temporary passcode page. If requested for a shared mailbox or distribution group, please wait a couple of minutes before requesting a new passcode as multiple emails may be sent to everyone in your shared mailbox or distribution list.
What if I am still having trouble signing in?
Please contact Barracuda Networks Technical Support at https://www.barracuda.com/support to help you log in or escalate your issue to the correct team.
Related Campus Articles:
]]>When end users open their email digests going forward, they can still click “Manage Quarantine” or “View Message Log” buttons. However, these buttons will now direct them to the EGD login page prior to taking them into their account. Users can authenticate with their EGD account email and password, or through LDAP or Azure AD.
Currently users that are members of a shared mailbox or distribution list will have to go through their account administrator to make adjustments to their quarantine mail. The EGD team is actively working on an alternative authentication approach for shared mailboxes.
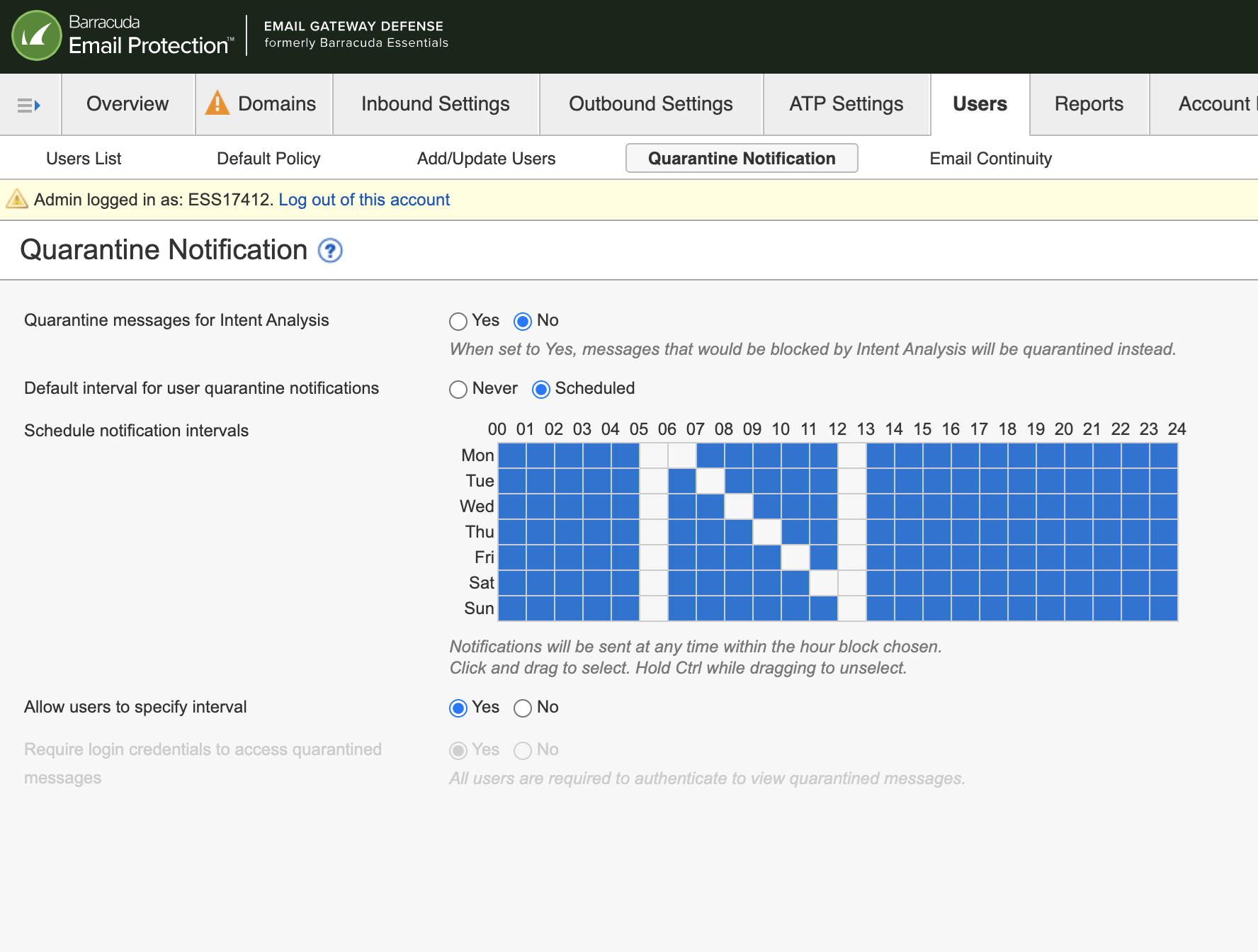
Admin feature "Require login credentials to access quarantined messages" Disabled:
When Admins log in and select the Users Tab à Quarantine Notification, there is a feature named “Require login credentials to access quarantined messages.” This feature has been enabled to “Yes” for all users and greyed out to ensure that all end users must log in to view their accounts.
Frequently Asked Questions (FAQs):
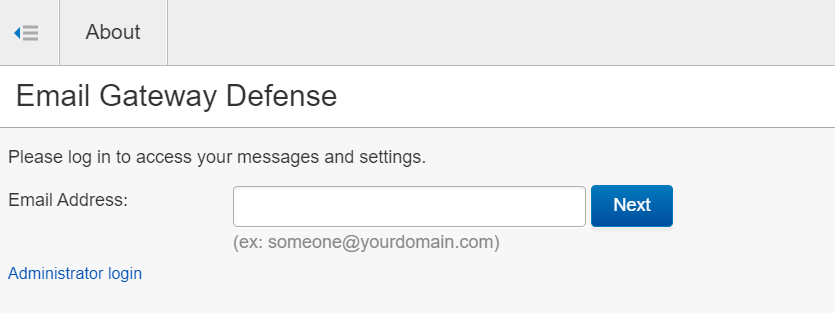
What if I don’t know my password?
If you have an EGD managed password/account login, you will be redirected to the EGD login page. Enter your email address and click “Next.”
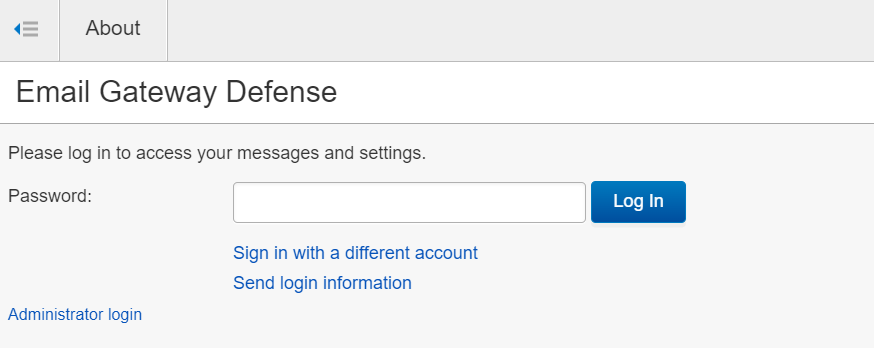
Once on the password submission page, click “Send login information.” This will trigger a password reset link to be sent to your email address. Go to your email to use the password reset link.
What if I use Azure AD or LDAP to login?
If your Admin has set you to have Azure AD or LDAP authentication with Single Sign-On, you will be automatically redirected to the AD or LDAP page for entering your credentials.
What if I am a member of a shared mailbox or distribution list?
If you are a member of a shared mailbox or distribution list, you will need contact your administrator to manage your quarantine, i.e. releasing an email or adding/removing a sender policy.
What if I am still having trouble logging in?
Please reach out to Customer Support at 1-408-342-5300. Our support team will be able to help you log in or escalate your concern to the EGD team.
]]>When end users open their email digests going forward, they can still click “Manage Quarantine” or “View Message Log” buttons. However, these buttons will now direct them to the EGD login page prior to taking them into their account. Users can authenticate with their EGD account email and password, or through LDAP or Azure AD.
Currently users that are members of a shared mailbox or distribution list will have to go through their account administrator to make adjustments to their quarantine mail. The EGD team is actively working on an alternative authentication approach for shared mailboxes.
Admin feature "Require login credentials to access quarantined messages" Disabled:
When Admins log in and select the Users Tab à Quarantine Notification, there is a feature named “Require login credentials to access quarantined messages.” This feature has been enabled to “Yes” for all users and greyed out to ensure that all end users must log in to view their accounts.

Frequently Asked Questions (FAQs):
What if I don’t know my password?
If you have an EGD managed password/account login, you will be redirected to the EGD login page. Enter your email address and click “Next.”

Once on the password submission page, click “Send login information.” This will trigger a password reset link to be sent to your email address. Go to your email to use the password reset link.

What if I use Azure AD or LDAP to login?
If your Admin has set you to have Azure AD or LDAP authentication with Single Sign-On, you will be automatically redirected to the AD or LDAP page for entering your credentials.
What if I am a member of a shared mailbox or distribution list?
If you are a member of a shared mailbox or distribution list, you will need contact your administrator to manage your quarantine, i.e. releasing an email or adding/removing a sender policy.
What if I am still having trouble logging in?
Please reach out to Customer Support at 1-408-342-5300. Our support team will be able to help you log in or escalate your concern to the EGD team.
]]>Barracuda has been working extremely hard over the past year to bring all our solutions to a new, modern, front-end technology stack (ReactJS). You may have already seen the new UI in our other solutions (Impersonation Protection and Incident Response). This new framework will allow us to build new UI features much quicker, which means faster updates for our customers. We are pleased to announce that the new React platform has now been launched on the end user interface of Email Gateway Defense.
Additional information to be aware of:
This platform launch is a 1-for-1 migration from the old framework, which means that there are no new features/capabilities at this time, just a new “skin” or “look and feel.” However, this migration will allow us to add new features or make changes to our products much more quickly in the future.
This launch is for the end user portion of the product only. We’ve begun work on the admin interface and will have a beta version available for users to try.
This new interface will be rolled out slowly to end users over the next 4 weeks to be completed by the end of May 2023.
Only accounts with a “User” role will see the new UI. If you have set a user as a “domain admin” or “helpdesk” role within EGD, they will need to be set to “user” in order to see the new UI. This is NOT the same thing as setting up an administrator through Barracuda Cloud Control.
Please see image below for an example of the new UI.
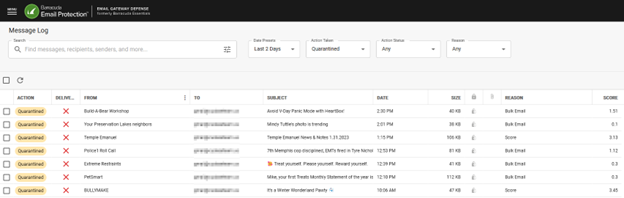
Barracuda has been working extremely hard over the past year to bring all our solutions to a new, modern, front-end technology stack (ReactJS). You may have already seen the new UI in our other solutions (Impersonation Protection and Incident Response). This new framework will allow us to build new UI features much quicker, which means faster updates for our customers. We are pleased to announce that the new React platform has now been launched on the end user interface of Email Gateway Defense.
Additional information to be aware of:
This platform launch is a 1-for-1 migration from the old framework, which means that there are no new features/capabilities at this time, just a new “skin” or “look and feel.” However, this migration will allow us to add new features or make changes to our products much more quickly in the future.
This launch is for the end user portion of the product only. We’ve begun work on the admin interface and will have a beta version available for users to try.
This new interface will be rolled out slowly to end users over the next 4 weeks to be completed by the end of May 2023.
Only accounts with a “User” role will see the new UI. If you have set a user as a “domain admin” or “helpdesk” role within EGD, they will need to be set to “user” in order to see the new UI. This is NOT the same thing as setting up an administrator through Barracuda Cloud Control.
Please see image below for an example of the new UI.

To require mail coming inbound to Email Gateway Defense to use a TLS connection, use the SMTP Encryption section on the Domains > Edit Settings page for each domain.
Use the Require TLS to Barracuda from these domains list to require a TLS connection from certain domains to Barracuda. You can manually add specific domains one at a time or use the Bulk Edit button.
Note: TLS provides secure transmission of email content, both inbound and outbound, over an encrypted channel using the Secure Sockets Layer (SSL). If a TLS connection cannot be established, then the mail will not be delivered.
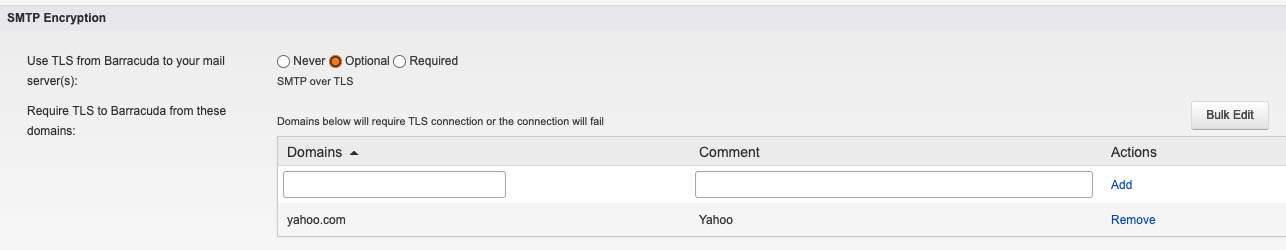
To require mail coming inbound to Email Gateway Defense to use a TLS connection, use the SMTP Encryption section on the Domains > Edit Settings page for each domain.
Use the Require TLS to Barracuda from these domains list to require a TLS connection from certain domains to Barracuda. You can manually add specific domains one at a time or use the Bulk Edit button.
Note: TLS provides secure transmission of email content, both inbound and outbound, over an encrypted channel using the Secure Sockets Layer (SSL). If a TLS connection cannot be established, then the mail will not be delivered.

Note that when you select Don’t Encrypt on a Message Content Filter and Encrypt on a Predefined Filter, the Message Content Filter exemption takes precedence over the Predefined Filter and the message will not be encrypted.
]]>Note that when you select Don’t Encrypt on a Message Content Filter and Encrypt on a Predefined Filter, the Message Content Filter exemption takes precedence over the Predefined Filter and the message will not be encrypted.
]]>